Cable viewers have again been endlessly inundated with Home Based Business advertisements claiming riches beyond your wildest dreams.
You know the one..."I made over $9000 last month working from home part-time."
Right...
Same message, different URL; they simply change the URL every so often. The current domain is 67gogreen.com, others have included crazyfox.com and 46homeworker.com.
All of this complete bulls**t is brought to you by LG Technologies of Temecula, CA, under the premise of Home Based Busines - As Seen on TV.
First, the fine print:
The incomes depicted are not typical and represent a small percentage of actual participants. There are no guarantees that participants will be able to achieve the income levels depicted.
Second, your privacy at risk:
We will maintain a record of your Personally Identifiable Information (PII) that will be sold or transferred to third parties that we believe offer products, services, and/or opportunities that are consistent with your expressed interests. Note that if you voluntarily provide us with Personally Identifiable Information, you consent to our sale, transfer, and use of your information.
Third, security:
We treat your Personally Identifiable Information very carefully and use our best efforts to protect your Personally Identifiable Information against unauthorized access and disclosure.
Do you now? Let's investigate...
HomeBusinessInstitution claims to be VeriSign Secured and are indeed using a Verisign cert. Thereafter, they display badges claiming "100% Safe Secure" and "100% Privacy Verified". Too bad they're both utter crap.
All measures of security (there aren't any) falter drastically, as homebusinessinstitution.com falls immediately to cross-site scripting (XSS).
To exemplify both my dismay and the lack of secure input validation, I offer the following screen shot of customized Javascript executing in the context of homebusinessinstitution.com.
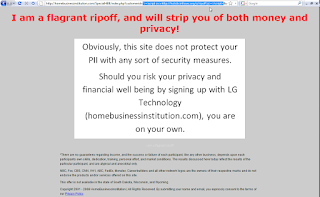
Companies such as this, who exploit the gullible and naive, infuriate me well before I endeavor to dissect their weak claims of securing your PII. To find that their victims are then at further risk leaves me blistering. It strikes me that only their vast disclaimer language serves to protect them from the likes of criminal prosecution or civil litigation.
There's an interesting study of LG Technology and their associates provided here.
I do hope someone finds a way of putting this likely fraud to an end.
del.icio.us | digg | Submit to Slashdot


