Update 2/6/09:
The March 2009 issue of toolsmith in the ISSA Journal will feature a complete review of Adito, including installation and usage. Expect the article to go live around 3/1/09.
In February 2006 I discussed SSL-Explorer, a project that is no longer supported.
It does however have new life in a project called Adito.
Much as SSL-Explorer was described, Adito is an open-source, browser-based SSL VPN solution. It's a remote access solution that provides users and businesses alike with a means of securely accessing network resources from outside the network perimeter using only a standard web browser.
Further:
Adito was forked from SSL-Explorer 1.0.0-rc17 for several reasons:
- To keep the already robust and functional open source codebase from decaying
- To reform SSL-Explorer (now Adito) from one company's product and a brand into a true community project
- To add new, exciting functionality
- To integrate existing functionality (e.g. sslexplorer-pam) into the program without the need to maintain it out of the source tree
This project shows updates as recently as December 19, 2008, and is in need of a developer so I'm hopeful maintenance and project enhancement will continue in earnest.
Give Adito a good look and let me know what you think; I may cover it in toolsmith.
del.icio.us | digg | Submit to Slashdot
Monday, December 29, 2008
Monday, December 22, 2008
Online finance flaw: Visa responds quickly to reported vulnerabilities
The American Express online flaw I discussed last week led to two interesting sidebars.
First, a rather strong media response resulted with coverage in The Register, BetaNews, and Dark Reading, amongst others.
Second, aside from all the variant hunters, I received a number of interesting finds from friend-of-the-cause Mike Bailey over at skeptikal.org.
He'd been inspired by the fact that the PoC I issued for the AmEx bug included an IFRAME insertion pointing to Visa.com. Inspiration led to discovery (and whole lot less work for me) and immediate issues were noted in a few Visa sites.
To be fair, http://usa.visa.com itself appears to be sound; both Mike and I gave it a cursory glance and nothing popped up (XSS pun).
The same could not be said for http://empresarial.visa.com.
No need to rehash all the problems XSS issues in major credit card company sites might cause (PCI compliance, phishing, customer abuse, etc.); earlier posts speak for themselves.
As always, I reported the vulns per my terms of engagement.
Here's where the rather unexpected occurred.
I first reported the issues on December 17th at 1322 hours PST.
They were fixed no later than December 18th at 1916 hours PST.
In essence, Visa executed a 24 hour turn around for mitigation and repair.
Now, I have no doubt variant hunters will likely go digging about for other vulnerabilities, and if Visa hasn't issued global repairs, they might find some.
But, what's key here is how quickly Visa responded. I must admit, after the debacle born of the AmEx issue, I wondered if I'd be asked to report the vulns through Visa's PR department, a method recommended by AmEx to report vulns to them. ;-)
Not only was my disclosure responded to in a very timely fashion, I received the following feedback:
"We appreciate you bringing this situation to our attention. Visa takes security matters very seriously. All impacted pages have been taken down while we remediate the XSS coding. As always, feel free to report any future abuses to: abuse@visa.com."
Hard to argue with that.
My impression (unsubstantiated) is that the vulnerable sites were the product of a 3rd party development team, serving Spanish speaking customers, given the fact that the vulnerable code was PHP, not typical of English language Visa properties.
For posterity's sake one of the vulns appeared as follows. There were other similar issues with different variables, different sub-domains, and partner sites, but you get the point.
XSS in empresarial.visa.com/por/glossario.php:

I'd like to issue a "well done" to Visa and those who responded so quickly.
I can only hope that pending disclosures to all the other credit card vendors, banks, and brokerages in the Online Finance Flaws pipeline are handled as quickly and openly.
Thanks again to Mike Bailey (mckt) for his contributions to the cause. You'll see more of his work in future posts.
del.icio.us | digg | Submit to Slashdot
First, a rather strong media response resulted with coverage in The Register, BetaNews, and Dark Reading, amongst others.
Second, aside from all the variant hunters, I received a number of interesting finds from friend-of-the-cause Mike Bailey over at skeptikal.org.
He'd been inspired by the fact that the PoC I issued for the AmEx bug included an IFRAME insertion pointing to Visa.com. Inspiration led to discovery (and whole lot less work for me) and immediate issues were noted in a few Visa sites.
To be fair, http://usa.visa.com itself appears to be sound; both Mike and I gave it a cursory glance and nothing popped up (XSS pun).
The same could not be said for http://empresarial.visa.com.
No need to rehash all the problems XSS issues in major credit card company sites might cause (PCI compliance, phishing, customer abuse, etc.); earlier posts speak for themselves.
As always, I reported the vulns per my terms of engagement.
Here's where the rather unexpected occurred.
I first reported the issues on December 17th at 1322 hours PST.
They were fixed no later than December 18th at 1916 hours PST.
In essence, Visa executed a 24 hour turn around for mitigation and repair.
Now, I have no doubt variant hunters will likely go digging about for other vulnerabilities, and if Visa hasn't issued global repairs, they might find some.
But, what's key here is how quickly Visa responded. I must admit, after the debacle born of the AmEx issue, I wondered if I'd be asked to report the vulns through Visa's PR department, a method recommended by AmEx to report vulns to them. ;-)
Not only was my disclosure responded to in a very timely fashion, I received the following feedback:
"We appreciate you bringing this situation to our attention. Visa takes security matters very seriously. All impacted pages have been taken down while we remediate the XSS coding. As always, feel free to report any future abuses to: abuse@visa.com."
Hard to argue with that.
My impression (unsubstantiated) is that the vulnerable sites were the product of a 3rd party development team, serving Spanish speaking customers, given the fact that the vulnerable code was PHP, not typical of English language Visa properties.
For posterity's sake one of the vulns appeared as follows. There were other similar issues with different variables, different sub-domains, and partner sites, but you get the point.
XSS in empresarial.visa.com/por/glossario.php:

I'd like to issue a "well done" to Visa and those who responded so quickly.
I can only hope that pending disclosures to all the other credit card vendors, banks, and brokerages in the Online Finance Flaws pipeline are handled as quickly and openly.
Thanks again to Mike Bailey (mckt) for his contributions to the cause. You'll see more of his work in future posts.
del.icio.us | digg | Submit to Slashdot
Tuesday, December 16, 2008
So...you can hack a server with XSS?
It's been awhile since I've updated you, dear reader, regarding matters concerning McAfee Secure.
You may recall I met with Joe Pierini and Kirk Lawrence of McAfee Secure in August, and received an update regarding the still pending "McAfee Secure Standard" in October.
Sadly, both Joe and Kirk have left McAfee, in pursuit of better opportunities, leaving our McAfee Secure crusade in lurch. I'll be updating you on the Standard (allegedly, now being released in January), and other proposed improvements to the McAfee Secure offering in days to come. I have been informed that there are people at McAfee willing to carry on the work that Joe and Kirk started.
Now, that said, an update from Joe Pierini. You may recall the numerous times I, and many others, have heckled Joe for his Pwnie award winning statement "Cross-site scripting can't be used to hack a server."
Joe has surprised me at more than one interval; first, attending the Pwnie Awards ceremony at BlackHat 2008, and later, agreeing to fly to Seattle to meet with me and discuss considering significant changes and improvements in the McAfee Secure program.
What I've learned of Joe is that he is technically capable, a worthy web application security assessor and pen tester in his own right, and someone who prefers "breaking things" in the trenches, as opposed to promoting brands as an SE.
Having had numerous conversations with Joe since August, I believe this: the debate sparked by his now infamous "can't hack a server with XSS" statement came down to semantics and context. To be fair, the act of dropping javascript strings behind a vulnerable GET parameter is not a server hack per se, particularly if not utilized in a hybrid attack.
But enough from me; Joe explains just such a hybrid approach quite elegantly in a letter I recently received from him. It is reprinted here with his permission, and I appreciate the opportunity to share it.
Russ,
As you know, I left McAfee Secure in early December to join a security firm in San Jose as a Security Consultant. We provide PCI assurance services related to Merchants, Financial Institutions, Processors and Service Providers. As soon as I complete the PCI Security Standards Council's Qualified Security Assessor (QSA) training course, I will be assuming the responsibilities as a QSA but in the mean time I am performing penetration tests for clients needing to meet the PCI 11.3 requirements.
In one of my first engagements, I came upon a situation where there were no critical vulnerabilities and a few minor issues including XSS and a couple of Exchange mail servers with an open relay misconfiguration. These findings are sufficient with which to take a merchant out of PCI compliance but they lack the drama and urgency of more serious vulnerabilities like SQL Injection. My infamous, award winning catch phrase, “You can’t hack a server with it”, came back to haunt me. While you and I have agreed this is technically true, the the 11.3 penetration tests I was conducting are intended to exploit vulnerabilities. What I needed was an attack scenario that would get their attention and demonstrate the risk of having XSS in the web site.
The mail servers would only allow mail relaying to email addresses within the domain. They would provide the perfect delivery mechanism for the attack. A remote web server could be configured to host the attack pages for XSS Shell. This application ( http://labs.portcullis.co.uk/application/xssshell/) makes use of concepts first presented by XSS Proxy over 3 years ago: persistent, bi-directional communication with a client machine using XSS. The XSS Shell makes it possible to log keystrokes, steal the clipboard, execute arbitrary javascript and more. I don't need to hack the server with it, I could attack the entire company.
First, I could craft an email pretending to be from the web development team asking for help in testing a new piece of functionality in the website. I could then embed an HTML link in the page directing them to their own website, albeit with an attack exploiting the XSS weakness in their web site appended to it. Because the company users would receive an email with all the right headers from their own mail server and directing them to a site they own and inherently trusted, the click through rate would be extremely high and I could collect the session and clip board content from dozens of users. If my instinct was correct, I wouldn't need to upload arbitrary javascript because I would have enough to prove my point: XSS is dangerous and poses an immediate risk.
It’s not just about the servers or the clients, XSS can leave the entire company vulnerable to attack.
Best Regards,
--
Joseph Pierini | CISSP, CISM
Best regards indeed. Thank you, Joe.
del.icio.us | digg | Submit to Slashdot
You may recall I met with Joe Pierini and Kirk Lawrence of McAfee Secure in August, and received an update regarding the still pending "McAfee Secure Standard" in October.
Sadly, both Joe and Kirk have left McAfee, in pursuit of better opportunities, leaving our McAfee Secure crusade in lurch. I'll be updating you on the Standard (allegedly, now being released in January), and other proposed improvements to the McAfee Secure offering in days to come. I have been informed that there are people at McAfee willing to carry on the work that Joe and Kirk started.
Now, that said, an update from Joe Pierini. You may recall the numerous times I, and many others, have heckled Joe for his Pwnie award winning statement "Cross-site scripting can't be used to hack a server."
Joe has surprised me at more than one interval; first, attending the Pwnie Awards ceremony at BlackHat 2008, and later, agreeing to fly to Seattle to meet with me and discuss considering significant changes and improvements in the McAfee Secure program.
What I've learned of Joe is that he is technically capable, a worthy web application security assessor and pen tester in his own right, and someone who prefers "breaking things" in the trenches, as opposed to promoting brands as an SE.
Having had numerous conversations with Joe since August, I believe this: the debate sparked by his now infamous "can't hack a server with XSS" statement came down to semantics and context. To be fair, the act of dropping javascript strings behind a vulnerable GET parameter is not a server hack per se, particularly if not utilized in a hybrid attack.
But enough from me; Joe explains just such a hybrid approach quite elegantly in a letter I recently received from him. It is reprinted here with his permission, and I appreciate the opportunity to share it.
Russ,
As you know, I left McAfee Secure in early December to join a security firm in San Jose as a Security Consultant. We provide PCI assurance services related to Merchants, Financial Institutions, Processors and Service Providers. As soon as I complete the PCI Security Standards Council's Qualified Security Assessor (QSA) training course, I will be assuming the responsibilities as a QSA but in the mean time I am performing penetration tests for clients needing to meet the PCI 11.3 requirements.
In one of my first engagements, I came upon a situation where there were no critical vulnerabilities and a few minor issues including XSS and a couple of Exchange mail servers with an open relay misconfiguration. These findings are sufficient with which to take a merchant out of PCI compliance but they lack the drama and urgency of more serious vulnerabilities like SQL Injection. My infamous, award winning catch phrase, “You can’t hack a server with it”, came back to haunt me. While you and I have agreed this is technically true, the the 11.3 penetration tests I was conducting are intended to exploit vulnerabilities. What I needed was an attack scenario that would get their attention and demonstrate the risk of having XSS in the web site.
The mail servers would only allow mail relaying to email addresses within the domain. They would provide the perfect delivery mechanism for the attack. A remote web server could be configured to host the attack pages for XSS Shell. This application ( http://labs.portcullis.co.uk/application/xssshell/) makes use of concepts first presented by XSS Proxy over 3 years ago: persistent, bi-directional communication with a client machine using XSS. The XSS Shell makes it possible to log keystrokes, steal the clipboard, execute arbitrary javascript and more. I don't need to hack the server with it, I could attack the entire company.
First, I could craft an email pretending to be from the web development team asking for help in testing a new piece of functionality in the website. I could then embed an HTML link in the page directing them to their own website, albeit with an attack exploiting the XSS weakness in their web site appended to it. Because the company users would receive an email with all the right headers from their own mail server and directing them to a site they own and inherently trusted, the click through rate would be extremely high and I could collect the session and clip board content from dozens of users. If my instinct was correct, I wouldn't need to upload arbitrary javascript because I would have enough to prove my point: XSS is dangerous and poses an immediate risk.
It’s not just about the servers or the clients, XSS can leave the entire company vulnerable to attack.
Best Regards,
--
Joseph Pierini | CISSP, CISM
Best regards indeed. Thank you, Joe.
del.icio.us | digg | Submit to Slashdot
Monday, December 15, 2008
Online finance flaw: American Express XSS
Updated again 12/19/08 (see end of post)
Our third entrant in the Online Finance Flaws series is one that truly perturbs me.
American Express came to my attention when setting up an online access account I was prompted to REDUCE the amount of characters in my password to eight or less. What?!
Luckily, my partner in alerting you to the absurd, Rafal Los, covered this issue nicely in May.
Of course, prompted by my irritation, I challenged myself to see what other truly inane security "features" American Express might be offering.
Here's where the trouble begins.
I kid you not, thirty seconds later, I found a new cross-site scripting (XSS) vulnerability right off the American Express primary search script (not one of three already posted on XSSed.com).
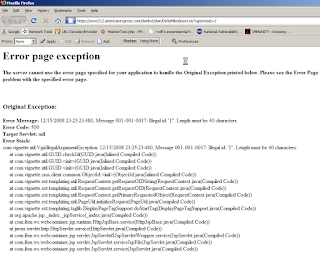
Three minutes later , in the TMI department, I discovered a most informative 500 error page exception indicating that American Express uses the Vignette CMS product via Apache and IBM's WebSphere.
Before I validate these findings please allow me to point you to the American Express data security page.
Key language includes:
"American Express is proud to be a founding member of the PCI Security Standards Council. The Council is designed to manage the ongoing evolution of the PCI Data Security Standard and to foster its broad adoption industry-wide. Through our participation with the Council, American Express continues our commitment to diligently pursue all aspects of data security."
Let me spell this out for you.
A founding member of the PCI Security Standards Council is itself in violation of PCI DSS 6.5.4.
This does little for my faith in American Express "data security", or the PCI Security Standards Council for that matter.
Finally, as always, I followed my terms of engagement in reporting these findings to American Express and was ignored by everyone including a director in their information security organization.
A video of both issues is here.
Should you prefer screen shots...an American Express XSS cookie grab:

Or the phishing warning:

Finally, my favorite, an IFRAME insertion of the VISA web site. Oops!

Oh yes, the 500 error, if you're still with me:
Is it wrong of me to expect more of credit card companies with claims to founding the PCI Security Standards Council? I think not.
Please contact American Express and register your own complaint. This is simply unacceptable.
Update 1100 hours 12/17/08:
American Express has made repairs regarding the XSS vulnerability, and has replied to Dan at The Register.
Additionally, this Computerworld article is just too silly and timely to not share in the context of our discussion. May the irony amuse you as much as it did me.
Update 2015 hours 12/19/08:
Repairs as indicated 12/17 now proven to be "repair" as variants galore arise.
Dan G. at The Register exposes research from at least two sources proving once again that one-off repairs are worthless when compared to a global approach.
Makes me wonder what this means for AmEx's stock.
Well done, fellow researchers. Well done.
del.icio.us | digg | Submit to Slashdot
Our third entrant in the Online Finance Flaws series is one that truly perturbs me.
American Express came to my attention when setting up an online access account I was prompted to REDUCE the amount of characters in my password to eight or less. What?!
Luckily, my partner in alerting you to the absurd, Rafal Los, covered this issue nicely in May.
Of course, prompted by my irritation, I challenged myself to see what other truly inane security "features" American Express might be offering.
Here's where the trouble begins.
I kid you not, thirty seconds later, I found a new cross-site scripting (XSS) vulnerability right off the American Express primary search script (not one of three already posted on XSSed.com).
Three minutes later , in the TMI department, I discovered a most informative 500 error page exception indicating that American Express uses the Vignette CMS product via Apache and IBM's WebSphere.
Before I validate these findings please allow me to point you to the American Express data security page.
Key language includes:
"American Express is proud to be a founding member of the PCI Security Standards Council. The Council is designed to manage the ongoing evolution of the PCI Data Security Standard and to foster its broad adoption industry-wide. Through our participation with the Council, American Express continues our commitment to diligently pursue all aspects of data security."
Let me spell this out for you.
A founding member of the PCI Security Standards Council is itself in violation of PCI DSS 6.5.4.
This does little for my faith in American Express "data security", or the PCI Security Standards Council for that matter.
Finally, as always, I followed my terms of engagement in reporting these findings to American Express and was ignored by everyone including a director in their information security organization.
A video of both issues is here.
Should you prefer screen shots...an American Express XSS cookie grab:

Or the phishing warning:

Finally, my favorite, an IFRAME insertion of the VISA web site. Oops!

Oh yes, the 500 error, if you're still with me:

Is it wrong of me to expect more of credit card companies with claims to founding the PCI Security Standards Council? I think not.
Please contact American Express and register your own complaint. This is simply unacceptable.
Update 1100 hours 12/17/08:
American Express has made repairs regarding the XSS vulnerability, and has replied to Dan at The Register.
Additionally, this Computerworld article is just too silly and timely to not share in the context of our discussion. May the irony amuse you as much as it did me.
Update 2015 hours 12/19/08:
Repairs as indicated 12/17 now proven to be "repair" as variants galore arise.
Dan G. at The Register exposes research from at least two sources proving once again that one-off repairs are worthless when compared to a global approach.
Makes me wonder what this means for AmEx's stock.
Well done, fellow researchers. Well done.
del.icio.us | digg | Submit to Slashdot
Tuesday, December 09, 2008
Online finance flaw: U.S. Bank & National City Bank XSS and more
Updated 12/24/08 (see end of post)
In this, our second entry in the series Online Finance Flaws, I call to your attention a report from Javelin Strategy & Research, the Banking Identity Safety Scorecard.
According to the MarketWatch writeup on the report, it "measures 25 leading U.S. financial institutions' customer-facing identity fraud capabilities. The Javelin model measures Prevention, Detection and Resolution(TM) features to track performance throughout the fraud cycle."
While I don't have the $1500 handy to purchase rights to read the complete report, it appears to be a comprehensive, well intended, ongoing effort.
Key questions asked by Javelin include:
1) Which financial institutions rank highest against Javelin’s customer-facing Prevention, Detection and Resolution™ criteria?
2) What type of account protection capabilities should banks and credit unions implement now to increase customer safety through Prevention, Detection and Resolution™?
3) Which customer safety features will most differentiate financial institutions in the future?
In answer to #1, the report lists its Top 5 indicating that Bank of America once again earned top overall honors, demonstrating excellence in its efforts to partner with customers against a crime that uniquely targets both the financial institution and the consumer. National City Bank (acquired by PNC) and Wells Fargo shared second position with equivalent scores followed closely by US Bank and Wachovia.
I'll answer #2 & #3 below.
I'll ask some further questions first, however.
Do we agree that web application security should and does play a critical role in what Javelin refers to as Prevention, Detection and Resolution™?
Do we agree that cross-site scripting (XSS), cross-site request forgery (CSRF), information disclosure, and SQL injection (SQLi) are all flaws that should not exist in a bank site on Javelin's Top 5?
Do we agree that XSS issues make for golden phishing opportunities for the inherently malicious, and again, should not exist in bank sites on Javelin's Top 5 with regard to a Banking Identity Safety Scorecard?
Before I discuss the flaws, be aware that I followed my terms of engagement with both of the following banks, and was largely ignored with either no reply or very vague, inconclusive brush-offs.
It is my hope that you, dear reader, will contact the following institutions, as I have, on behalf of the consumers they are obligated to protect, in the hope that they will make timely repairs.
And here, as I am prone to saying, is where the trouble begins.
U.S. Bank is vulnerable to XSS at their logon page.
National City Bank is vulnerable to XSS and information disclosure, as well as potential CSRF and potential SQLi, in a Cold Fusion (gasp!) app that runs a subdomain; specifically insights.nationalcity.com.
While the potential National City Bank vulns don't necessarily give a malicious attacker a ton to work with, given that it's an isolated app running a subdomain, the XSS issue is still useful in obvious ways.
I am particularly saddened by the XSS issue on the U.S. Bank site given the history of exploitation of just opportunities. See what I call the Italian Bank Job, and the article I wrote, Anatomy of an XSS Attack, inspired by the Italian caper.

Note that, as indicated in the Netcraft article on the Italian bank issue, SSL "security" is a moot point. Any script execution in the context of the U.S. Bank site occurs "protected" by SSL. As Netcraft says, "any SSL certificate associated with the site - included Extended Validation certificates - would display a padlock icon and apparently assure the user that the injected login form is genuine."
The National City Bank issues appear as follows.
XSS:

Information disclosure and potential SQLi both appear in the grossly verbose, overly helpful Cold Fusion error:

As a technical evangelist for online consumer well-being, and an information security practitioner, I'm here to tell you: these vulnerablities are indicative of behavior unbecoming of secure online banking; particularly as applied to two of the five "top-ranked banks who partner with customers to protect against identity fraud."
To answer #2 and #3 from above: build secure web applications.
U.S. Bank and National City Bank, I ask you to resolve these issues soon, on behalf of customers in your care.
Update 12/24/08:
U.S. Bank has notified me that they've repaired the vulnerable login code. Additionally, they've asked that I remove the video PoC, a request I choose to honor in deference to their open communication during the remediation period.
I've heard nothing from National City Bank. That said, while the initially reported issues appear to have been resolved, the resulting error message is still sloppy and overly informative (typical of Cold Fusion left unchecked).
del.icio.us | digg | Submit to Slashdot
In this, our second entry in the series Online Finance Flaws, I call to your attention a report from Javelin Strategy & Research, the Banking Identity Safety Scorecard.
According to the MarketWatch writeup on the report, it "measures 25 leading U.S. financial institutions' customer-facing identity fraud capabilities. The Javelin model measures Prevention, Detection and Resolution(TM) features to track performance throughout the fraud cycle."
While I don't have the $1500 handy to purchase rights to read the complete report, it appears to be a comprehensive, well intended, ongoing effort.
Key questions asked by Javelin include:
1) Which financial institutions rank highest against Javelin’s customer-facing Prevention, Detection and Resolution™ criteria?
2) What type of account protection capabilities should banks and credit unions implement now to increase customer safety through Prevention, Detection and Resolution™?
3) Which customer safety features will most differentiate financial institutions in the future?
In answer to #1, the report lists its Top 5 indicating that Bank of America once again earned top overall honors, demonstrating excellence in its efforts to partner with customers against a crime that uniquely targets both the financial institution and the consumer. National City Bank (acquired by PNC) and Wells Fargo shared second position with equivalent scores followed closely by US Bank and Wachovia.
I'll answer #2 & #3 below.
I'll ask some further questions first, however.
Do we agree that web application security should and does play a critical role in what Javelin refers to as Prevention, Detection and Resolution™?
Do we agree that cross-site scripting (XSS), cross-site request forgery (CSRF), information disclosure, and SQL injection (SQLi) are all flaws that should not exist in a bank site on Javelin's Top 5?
Do we agree that XSS issues make for golden phishing opportunities for the inherently malicious, and again, should not exist in bank sites on Javelin's Top 5 with regard to a Banking Identity Safety Scorecard?
Before I discuss the flaws, be aware that I followed my terms of engagement with both of the following banks, and was largely ignored with either no reply or very vague, inconclusive brush-offs.
It is my hope that you, dear reader, will contact the following institutions, as I have, on behalf of the consumers they are obligated to protect, in the hope that they will make timely repairs.
And here, as I am prone to saying, is where the trouble begins.
U.S. Bank is vulnerable to XSS at their logon page.
National City Bank is vulnerable to XSS and information disclosure, as well as potential CSRF and potential SQLi, in a Cold Fusion (gasp!) app that runs a subdomain; specifically insights.nationalcity.com.
While the potential National City Bank vulns don't necessarily give a malicious attacker a ton to work with, given that it's an isolated app running a subdomain, the XSS issue is still useful in obvious ways.
I am particularly saddened by the XSS issue on the U.S. Bank site given the history of exploitation of just opportunities. See what I call the Italian Bank Job, and the article I wrote, Anatomy of an XSS Attack, inspired by the Italian caper.

Note that, as indicated in the Netcraft article on the Italian bank issue, SSL "security" is a moot point. Any script execution in the context of the U.S. Bank site occurs "protected" by SSL. As Netcraft says, "any SSL certificate associated with the site - included Extended Validation certificates - would display a padlock icon and apparently assure the user that the injected login form is genuine."
The National City Bank issues appear as follows.
XSS:

Information disclosure and potential SQLi both appear in the grossly verbose, overly helpful Cold Fusion error:

As a technical evangelist for online consumer well-being, and an information security practitioner, I'm here to tell you: these vulnerablities are indicative of behavior unbecoming of secure online banking; particularly as applied to two of the five "top-ranked banks who partner with customers to protect against identity fraud."
To answer #2 and #3 from above: build secure web applications.
U.S. Bank and National City Bank, I ask you to resolve these issues soon, on behalf of customers in your care.
Update 12/24/08:
U.S. Bank has notified me that they've repaired the vulnerable login code. Additionally, they've asked that I remove the video PoC, a request I choose to honor in deference to their open communication during the remediation period.
I've heard nothing from National City Bank. That said, while the initially reported issues appear to have been resolved, the resulting error message is still sloppy and overly informative (typical of Cold Fusion left unchecked).
del.icio.us | digg | Submit to Slashdot
Wednesday, December 03, 2008
Online Finance Flaw: TIAA-CREF XSS & Potential CSRF
Update 12/4/08: TIAA-CREF has made appropriate repairs, and is no longer vulnerable to common XSS in the search.jsp script. I applaud their responsiveness.
Before discussing a TIAA-CREF security flaw, allow me to clarify my "terms of engagement".
Prior to offering analysis of any security flaws in online financial services, be assured I have engaged the service provider and offered what I believe to a reasonable amount of time to remedy this issue. Specifically, a minimum of two weeks and three unique contact attempts are made. Should the vendor offer a timeline in which the issue will be resolved, so long as it is not months or years, I will wait until they are ready to deploy the fix, then discuss the vulnerability. If I am not in receipt of a reply other than generic customer service replies, I will follow the two week standard, then discuss the issue.
TIAA-CREF, or the Teachers Insurance and Annuity Association - College Retirement Equities Fund, is a respected, widely utilized provider of numerous financial products and services. The TIAA-CREF site is ranked 26,148 on Alexa.com at the time of this writing.
I'll first direct you to the TIAA-CREF Security page, where they discuss the expected elements like identity theft, spoofing, tips, and my favorite, phishing.
Here's where the trouble begins. Obviously, most phishing occurs when some miscreant creates a fake page and attempts to lure victims via email.
The severity of phishing risks are greatly increased by the introduction of a cross-site scripting (XSS) vulnerability in a site that is of high value to phishing attackers.
With such a vulnerability available, the prospect of success for a phisher are much higher given that the malicious URL they would craft could include the actual target domain, rather than a faked misrepresentation. A simple script insertion at the vulnerable variable would then allow the attacker to redirect victims to a maliciously crafted logon page in the context of the vulnerable site.
Sad side note: when you search security at the TIAA-CREF site, the above mentioned Security page is not returned in the results as I write this.
However, the resulting search URL serves as the starting point for our discussion of the flaw:
http://www.tiaa-cref.org/explore/portlets/search.jsp?query=security&strtfrm=1&totpresults=75&srchtype=4&sc=1&frmsite=0
The vast majority of non-search input variables on the TIAA-CREF site offer reasonable XSS protections, likely a blacklist method that redirects you to the following language when common XSS strings are noted, particularly where it counts at logon pages.
Due to the presence of characters known to be used in Cross Site Scripting attacks, access is forbidden. This web site does not allow Urls which might include embedded HTML tags.
Unfortunately, this methodology was not deployed globally, and thus the following online finance flaw.
All input variables used in TIAA-CREF's search.jsp script are vulnerable to XSS.
Utilized by an attacker, this could have a much more significant impact on TIAA-CREF customers who fall victim to a now more convincing social engineering effort.
Here's the site before script insertion:

Here's the site after script insertion:

Further, certain parts of the site, including the Trust Company logon page, show potential signs of cross-site request forgery (CSRF) in that they accept updates via GET or allow submittal with the referrer stripped.
Lessons learned:
1) Don't assume all is well even though a site may offer examples of how attentive they are to security.
2) Never log on to an online financial service offering (or anything else for that matter) via a link sent to you in an email. Period.
3) Take all steps at your disposal to ensure you are logging in to and transacting with the actual site you intended to utilize. Don't depend on security badges and SSL certificates as your sole means of confirmation.
4) If you note something of concern at a site you utilize, advise them immediately and demand repair or clarification until you're satisfied.
Please feel free to send feedback to TIAA-CREF as I have per my "terms of engagement" above. Hopefully they'll resolve this issue soon, on behalf of customers in their care.
Up next in our series, two of the top five banks mentioned in Javelin Strategy & Research's Banking Identity Safety Scorecard are vulnerable to similar issues.
del.icio.us | digg | Submit to Slashdot
Before discussing a TIAA-CREF security flaw, allow me to clarify my "terms of engagement".
Prior to offering analysis of any security flaws in online financial services, be assured I have engaged the service provider and offered what I believe to a reasonable amount of time to remedy this issue. Specifically, a minimum of two weeks and three unique contact attempts are made. Should the vendor offer a timeline in which the issue will be resolved, so long as it is not months or years, I will wait until they are ready to deploy the fix, then discuss the vulnerability. If I am not in receipt of a reply other than generic customer service replies, I will follow the two week standard, then discuss the issue.
TIAA-CREF, or the Teachers Insurance and Annuity Association - College Retirement Equities Fund, is a respected, widely utilized provider of numerous financial products and services. The TIAA-CREF site is ranked 26,148 on Alexa.com at the time of this writing.
I'll first direct you to the TIAA-CREF Security page, where they discuss the expected elements like identity theft, spoofing, tips, and my favorite, phishing.
Here's where the trouble begins. Obviously, most phishing occurs when some miscreant creates a fake page and attempts to lure victims via email.
The severity of phishing risks are greatly increased by the introduction of a cross-site scripting (XSS) vulnerability in a site that is of high value to phishing attackers.
With such a vulnerability available, the prospect of success for a phisher are much higher given that the malicious URL they would craft could include the actual target domain, rather than a faked misrepresentation. A simple script insertion at the vulnerable variable would then allow the attacker to redirect victims to a maliciously crafted logon page in the context of the vulnerable site.
Sad side note: when you search security at the TIAA-CREF site, the above mentioned Security page is not returned in the results as I write this.
However, the resulting search URL serves as the starting point for our discussion of the flaw:
http://www.tiaa-cref.org/explore/portlets/search.jsp?query=security&strtfrm=1&totpresults=75&srchtype=4&sc=1&frmsite=0
The vast majority of non-search input variables on the TIAA-CREF site offer reasonable XSS protections, likely a blacklist method that redirects you to the following language when common XSS strings are noted, particularly where it counts at logon pages.
Due to the presence of characters known to be used in Cross Site Scripting attacks, access is forbidden. This web site does not allow Urls which might include embedded HTML tags.
Unfortunately, this methodology was not deployed globally, and thus the following online finance flaw.
All input variables used in TIAA-CREF's search.jsp script are vulnerable to XSS.
Utilized by an attacker, this could have a much more significant impact on TIAA-CREF customers who fall victim to a now more convincing social engineering effort.
Here's the site before script insertion:

Here's the site after script insertion:

Further, certain parts of the site, including the Trust Company logon page, show potential signs of cross-site request forgery (CSRF) in that they accept updates via GET or allow submittal with the referrer stripped.
Lessons learned:
1) Don't assume all is well even though a site may offer examples of how attentive they are to security.
2) Never log on to an online financial service offering (or anything else for that matter) via a link sent to you in an email. Period.
3) Take all steps at your disposal to ensure you are logging in to and transacting with the actual site you intended to utilize. Don't depend on security badges and SSL certificates as your sole means of confirmation.
4) If you note something of concern at a site you utilize, advise them immediately and demand repair or clarification until you're satisfied.
Please feel free to send feedback to TIAA-CREF as I have per my "terms of engagement" above. Hopefully they'll resolve this issue soon, on behalf of customers in their care.
Up next in our series, two of the top five banks mentioned in Javelin Strategy & Research's Banking Identity Safety Scorecard are vulnerable to similar issues.
del.icio.us | digg | Submit to Slashdot
Tuesday, December 02, 2008
Actns/Swif.T virus found in YouTube videos
TOOLS FOR FLASH ANALYSIS
Update 13:35 PDT: False positive finding from CA triggering on System.security.allowDomain("*").
Regardless, these two sites are indispensable for their quick analytic capability.
Seeing System.security.allowDomain("*") as problematic in not necessarily wrong as it often indicates malicious content.
Breaking news regarding malicious Flash popping up from YouTube is starting to break all over the Internet.
CrunchGear has a bit of a write-up on it.
Rather than sound off about what will become old news quickly, I'd like to point you to resources I use to analyze (or have the analysis done for me, to be more concise) malicious Flash or JavaScript.
I grabbed the evil .swf in question from the URL below via command-line on my trusty Ubuntu box:
wget hxxp://www.youtube.com/v/O7tB1pYSNuE&rel=1
I then fed l.swf to Adops Tools and Wepawet.
The results from each analysis are below for your review.
Note System.security.allowDomain("*").
Not good. ;-)
Adops Tools Results
Wepawet Results
Use in good faith, but always be careful grabbing the evil .swf.
del.icio.us | digg | Submit to Slashdot
Update 13:35 PDT: False positive finding from CA triggering on System.security.allowDomain("*").
Regardless, these two sites are indispensable for their quick analytic capability.
Seeing System.security.allowDomain("*") as problematic in not necessarily wrong as it often indicates malicious content.
Breaking news regarding malicious Flash popping up from YouTube is starting to break all over the Internet.
CrunchGear has a bit of a write-up on it.
Rather than sound off about what will become old news quickly, I'd like to point you to resources I use to analyze (or have the analysis done for me, to be more concise) malicious Flash or JavaScript.
I grabbed the evil .swf in question from the URL below via command-line on my trusty Ubuntu box:
wget hxxp://www.youtube.com/v/O7tB1pYSNuE&rel=1
I then fed l.swf to Adops Tools and Wepawet.
The results from each analysis are below for your review.
Note System.security.allowDomain("*").
Not good. ;-)
Adops Tools Results
Wepawet Results
Use in good faith, but always be careful grabbing the evil .swf.
del.icio.us | digg | Submit to Slashdot
Monday, December 01, 2008
Safe Keeping: Article on TrueCrypt in Information Security

My article, Safe Keeping, regarding TrueCrypt, is now available in Information Security magazine.
TrueCrypt is an open source laptop encryption alternative for your organization.
This article also includes a sidebar on Adeona, an open source system for tracking the location of your lost or stolen laptop that does not rely on a proprietary, central service.

I humbly suggest that you consider using both should you lack commercial solutions.
Cheers.
del.icio.us | digg | Submit to Slashdot
Subscribe to:
Posts (Atom)
Moving blog to HolisticInfoSec.io
toolsmith and HolisticInfoSec have moved. I've decided to consolidate all content on one platform, namely an R markdown blogdown sit...
-
toolsmith and HolisticInfoSec have moved. I've decided to consolidate all content on one platform, namely an R markdown blogdown sit...
-
When, in October and November 's toolsmith posts, I redefined DFIR under the premise of D eeper F unctionality for I nvestigators in R ...
-
You can have data without information, but you cannot have information without data. ~Daniel Keys Moran Here we resume our discussion of ...


