While Maltego includes numerous highly useful entities and transforms, it does not currently feature the ability to directly manipulate native PCAP files.
This is not entirely uncommon amongst other tools, particularly those specific to visualization; often such tools consume CSV files.
With thanks to Andrew MacPherson of Paterva for creating these for me upon request for recent presentations, I'm pleased to share with you Maltego local transforms that will render CSVs created from PCAP files. Simple, but extremely useful.
I'll take you step by step through the process, starting with creating CSVs from PCAPs.
For those of you already comfortable with PCAP to CSV conversion and/or using local transforms with Maltego, here are the pyCSV transforms:
GetSourceClients.py
GetDestinationClients.py
All others, read on.
Raffael Marty's AfterGlow (version 1.6 just released) includes tcpdump2csv.pl which uses tcpdump/windump to read a PCAP file and parse it into parametrized CSV output.
Windows users, assuming that Perl is installed and all files and scripts reside in the same directory, execute:
windump -vttttnnelr example.pcap | perl tcpdump2csv.pl "sip dip dport" > example.csv.
Linux users:
tcpdump -vttttnnelr example.pcap | tcpdump2csv.pl "sip dip dport" > example.csv
To integrate the pyCSV local transforms with your Maltego instance:
1. Click Tools, then Manage Transforms.
2. Click New Local Transforms.
3. Define the Display name as the name of the local transform. Example: GetSourceClients
4. Each transform must map to an entity. Do so as follows for
each transform as you create it:
getSourceClients to Phrase
getDestinationClients to IP Address
5. Click Next.
6. The Command field should point to Python binary (C:\Python25\python.exe on Windows, /usr/bin/python
on Ubuntu 9.10).
7. The Parameters field should refer only to the transform name. Example: GetSourceClients.py
8. Work Directory should be the complete path to the directory where you keep the Nmap local transform Python scripts (suggest C:\localTransforms\pyCSV for Windows users).
9. Finish, then Save.
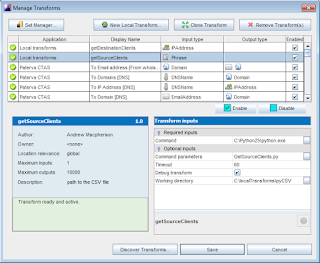
You'll also need a copy MaltegoTransform.py in your local transforms directory (included with the Maltego python lib during installation).
During a recent Zeus bot investigation, I used GetSourceClients.py and GetDestinationClients.py as follows:
1) Convert zeus.pcap, captured during malware analysis in a virtual ennvironment,
to zeus.csv: tcpdump -vttttnnelr zeus.pcap | tcpdump2csv.pl "sip dip dport" > zeus.csv
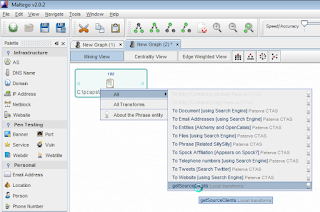
2) Drag a Phrase entity into the Maltego workspace, and using CopyPath, pasted the full path to the zeus.csv into the Phrase entity.
3) Right-clicked the Phrase entity, chose All, then getSourceClients.
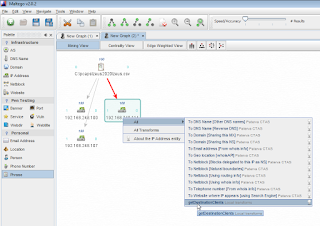
4) Right-clicked the IP entity created for my infected host, chose All, then getDestinationClients.
5) Egress traffic to a likely malicious host immediately jumped out of the Maltego workspace at me. I right-clicked (after removing the port reference in the IP entity label) and selected AllTransforms.
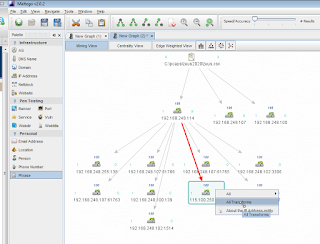
6) Maltego's results were swift and validated my immediate assumption. 115.100.250.105 is a malicious Chinese (omg, really?) Zeus C&C server. Nice.
Highlighting a Website entity then choosing Detail View will tell you everything you need to know.
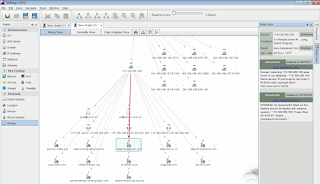
"Size matters not. Look at me. Judge me by my size, do you? Hmm? Hmm. And well you should not. For my ally is Maltego, and a powerful ally it is."
Yoda's right. ;-)
If you have any questions or would like saved transforms, PCAPs, or binary samples, ping me at russ at holisticinfosec dot org.
Cheers.
del.icio.us | digg | Submit to Slashdot
Please support the Open Security Foundation (OSVDB)



No comments:
Post a Comment