With some of my new found flexibility (not bound to print deadlines) I'm now able to provide near-realtime toolsmith content in direct response to recommendations or interaction via social media (
@holisticinfosec), and other avenues. Just another service provided by your friendly neighborhood toolsmith. :-) Such is the case as we discuss Erik Hjelmvik's
CapLoader. We're connecting a few strands in our beautifully enmeshed community here. First, we discussed Erik's outstanding
NetworkMiner in November 2011. Erik's tools have done nothing but improve since, and CapLoader, as part of those regular improvements, came to fruition to answer the "large file" problem. Second, in May 2015, when I discussed
Hunting in-memory adversaries with Rekall and WinPmem I created a fairly sizable memory image (5GB) that included network activity from a compromised host to an attacker-controlled resource. When, via
Twitter, I announced that I'm presenting related content to a
2015 Northwest Regional ICAC Conference audience on 5 OCT, Erik replied to remind me that, if I hadn't already, to try and carve packets from my memory dump with CapLoader, and that I'll be amazed. As a jaded, crusty, and exponentially aging security practitioner, I'm not easily amazed, so I took the challenge and told him "I'm going to do u one better. Next #toolsmith to be about CapLoader inspecting the memory image specifically created for this talk." And here we are! The HolisticInfoSec circle of life.
As CapLoader's network carving from memory feature has been available for more than a year, and it was nicely written up for you on the Netresec blog, I'll point you to Erik's March 2014
post as your starting point, along with the above mentioned WinPmem/Rekall
article. CapLoader is easily downloaded and installed on modern Windows systems, your only dependency is .NET Framework 4.0. The free version will provide all the network packet carving magic you need, but I also tested the commercial version with a license provided by Erik.
I'm going to give you some perfomance benchmarks as well as we go along.
Here's how easy it was to put CapLoader 1.3.1 Trial to use on the
compromised.raw memory image from the WinPmem/Rekall
article.
- Opened CapLoader
- Selected File then Carve Packets from File
- Selected compromised.raw from Open dialog
- Under Input Settings, left Create Gantt chart, Build hosts list, and Parse DNS enabled. The additional options aren't available in the free version. We'll discuss the licensed version features and performance below,
- Left all Carving Options enabled and clicked Start as seen in Figure 1.
 |
| Figure 1: CapLoader memory image network carving options |
Exactly 76 seconds later, the free, trial version of CapLoader extracted 32 flows from 23 hosts from a 5GB memory image acquired via WinPmem. Sorry, this isn't amazing, it's amazeballs. I can't express how fast that is for functionality of this nature. There, awaiting further analysis, was
compromised.raw.pcapng. Better still, I wanted to just focus on flows for two hosts, 192.168.177.130 (attacker) and 192.168.177.129 (victim). CapLoader includes an
Auto-extract flows on select feature, I just highlighted these two flows, and BLAM!, they were written out to a new PCAPNG file as seen in
Figure 2.
 |
| Figure 2: Selected flows |
Just double-click the PCAP CapLoader logo in the upper-right quadrant of the CapLoader UI and it'll open the selected flows in Wireshark (if installed) automatically. You can also just click
File then
Save Selected Flows. In addition to Wireshark analysis, what's the most obvious next step given that we're talking about a Netresec tool here? Yes! Use
NetworkMiner. One small note: if you have any issues moving between PCAPNG and PCAP files (the free version of NetworkMiner doesn't open PCAPNG files) you can use
PcapNG.com (also a Netresec service) to convert captures smaller than 8MB.
I repeated the exercise with the commercial version of CapLoader with two additional features enabled,
Identify Protocols and
Show Countries, and in 72 seconds (four seconds faster than our first run with the trial version) had my results.
After all this though, the resulting network capture was not much use as I had pushed my Meterpreter session for the Rekall discussion over HTTPS, but you get the point. Had network traffic ensued via a clear-text protocol, CapLoader's ability to rapidly carve it out of a memory image would have been invaluable.
To prove that point, I'll give you one quick unrelated example. Using the commercial copy of CapLoader, I loaded a different memory image where misuse of MSN Messenger was in play. In exactly 22 seconds for this 1GB memory image, and a bit of column sorting, I was able to instantly visualize the Messeger traffic using the CapLoader Gantt feature as seen in
Figure 3.
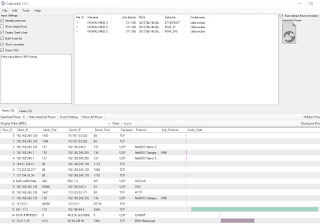 |
| Figure 3: CapLoader Gantt chart visual |
CapLoader is wonderful stuff indeed from Erik and Netresec, loved the suggestion to explore it in the context of the
Hunting in-memory adversaries with Rekall and WinPmem presentation, and as always, look forward to what's next from Erik. Follow Erik via
@netresec and ping me via email or Twitter if you have questions (russ at holisticinfosec dot org or
@holisticinfosec).
Cheers…until next time.








No comments:
Post a Comment